By Joanna Dempsey
Vice President, CISA Portfolio
and Keith McCloskey
Vice President, Justice & Homeland Solutions, CTO
[This article complements a talk given by Joanna Dempsey, vice president of CISA portfolio at ECS, at ElasticON 2023. Click here to view Joanna’s full presentation on YouTube.]
For the past three years, ECS has been working with the Cybersecurity and Infrastructure Security Agency (CISA) Continuous Diagnostics and Mitigation (CDM) program to build, deploy, and operationalize a whole new CDM dashboard ecosystem. Our goal has been realizing actionable operational visibility for federal agencies – an unprecedented level of visibility and access to cyber data, at scale. The CDM Dashboard ecosystem improves how incident responders find and remediate threats and vulnerabilities, enabling agencies to better protect their assets.
To achieve this, we’ve partnered with Elastic, whose suite of open-source products enables real-time search, analysis, and visualization of data regardless of format. And while the original CDM mission to help federal agencies protect their networks remains strong, the CDM dashboards, built on Elastic, are enabling a game-changing level of visibility and insight. After exploring how, we’ll look at a scenario illustrating how operational visibility in the federal government could greatly improve our nation’s cybersecurity.


The First Steps Towards Operational Visibility
First, we must recognize the impact of the 2021 Executive Order on cybersecurity, which did three critical things:
- Removed many of the government’s barriers for interagency data sharing.
- Directed the improved collection and analysis of additional cyber-relevant data.
- Prescribed a government-wide endpoint detection and response (EDR) capability, which has become a top priority for CDM.
This evolution of federal cyber requirements cleared a path for more effective collaboration across the federal civilian executive branch (FCEB) agencies – a new direction that aligned perfectly with platforms like Elastic and the CDM dashboards.
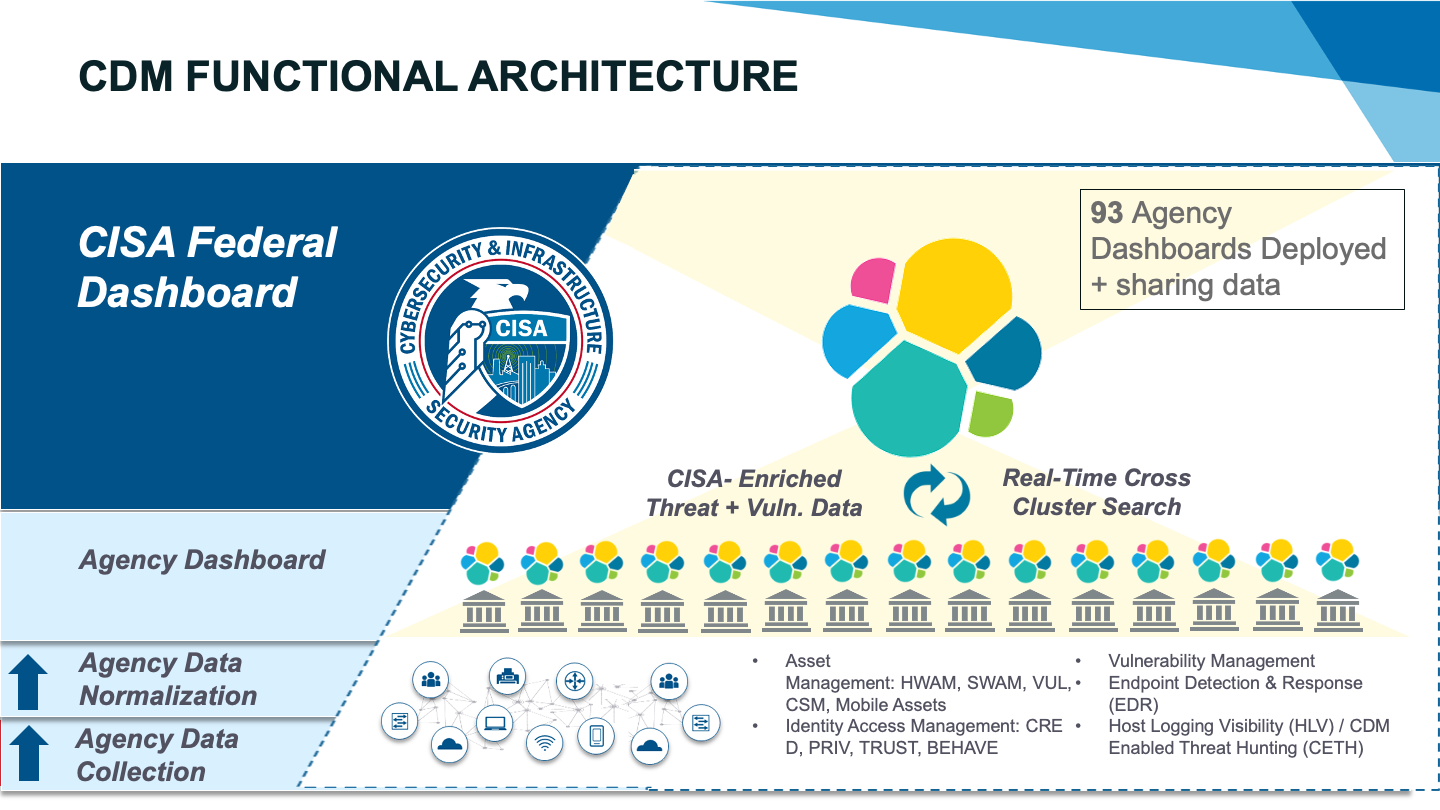
The CDM Agency Dashboard is the first point at which all these vast data sets are aggregated so that we can efficiently scale federal cyber operations.
Starting at the bottom of this chart, we have a diverse and dynamic set of agency tools and sensors that satisfy a range of requirements for effective cyber hygiene on agency networks. Moving up a layer, the data from these tools and sensors is integrated and aligned to a common schema so that we can make sense of it at scale.
CDM and Operational Visibility
CISA’s operational visibility strategy has two components:
- Providing improved, contextualized visibility into an organization’s mission.
- Providing deeper insights into the risk posture of an organization and its assets.
The strategy’s goal is to connect people with the right contextualized and enriched data to help them make better decisions and reduce cyber risk. In the agency’s view, the question operational visibility seeks to answer is:
“How do we integrate the people, processes, and tools we need to automate the detection and remediation of the known, predict the known unknowns, and adapt to the unknown unknowns?”
Let’s focus on two key initiatives within CDM that enable CISA’s operational visibility strategy: the government-wide deployment of EDR capabilities and a Host Logging Visibility pilot. The former has become a critical part of federal cyber programs, as EDR tools are generally very good at automating the detection and remediation of known bad things happening on an endpoint. The latter expands the data available to agency and CISA analysts in the CDM dashboard to include endpoint logs – data which can be correlated at scale and with other CISA intelligence to improve threat detection and analysis.
Operational Visibility in Action
Now, let’s walk through exactly how the CDM dashboards can help orchestrate an improved defense of agency networks.
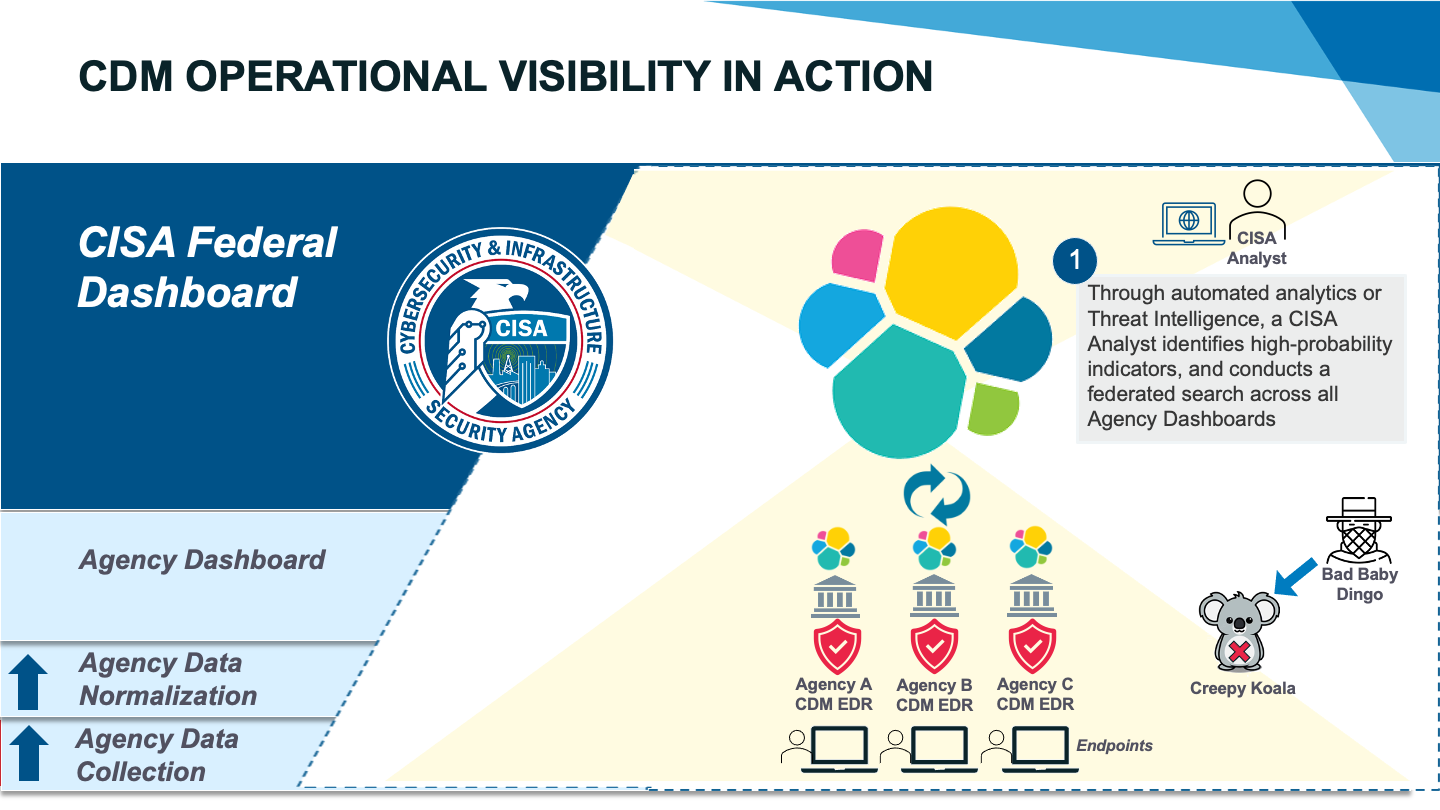
Pretend you’re a CISA cyber analyst tracking a particularly bad threat actor, “Bad Baby Dingo,” operating out of Australia. You receive intelligence that Bad Baby Dingo is targeting a common vulnerability and exposure (CVE) to launch a rare process that installs a malicious file on victims’ systems.
The process to install the file, which we’ll call “Creepy Koala,” leaves behind clues – specifically, logs that describe the process being launched and the file being installed. These process logs are captured on the endpoint and sent to the CDM dashboard for analysis and monitoring.
You log in to the CDM federal dashboard and run a search across the entire FCEB for the CVE that Bad Baby Dingo is exploiting. You get over 12,000 hits spread across 14 agencies, which would require a huge amount of labor to comb over. However, with the dashboard, you simply isolate the assets with the CVE, gaining insights into potential high value assets (HVAs) that could be impacted. Using this list as your input for another query, you identify potential indicators that the Creepy Koala process has been run. This time, your search leads you to 18 devices split between just two agencies, with HVA context to help inform and prioritize your response.
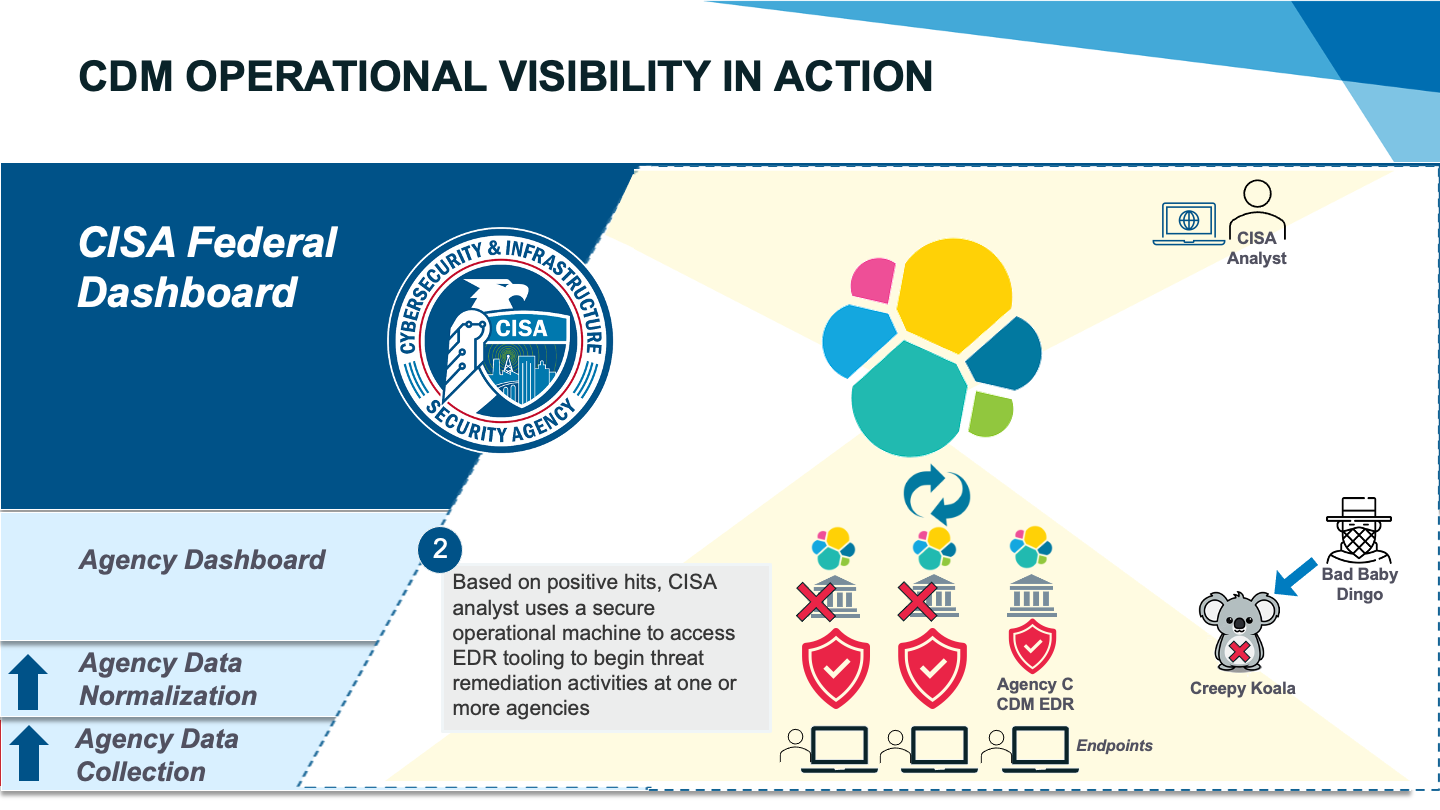
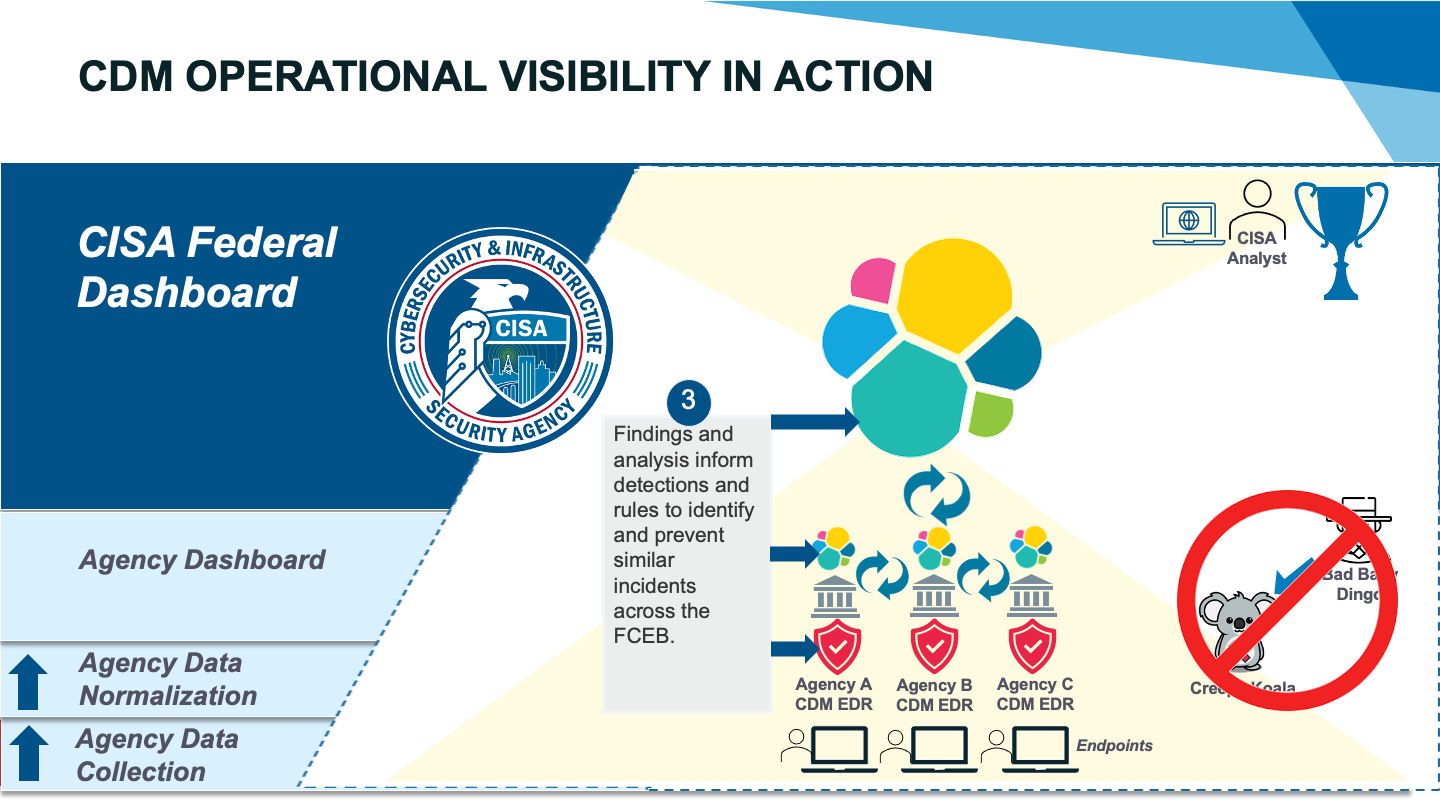
At this point, you have evidence that Bad Baby Dingo has breached two federal networks with an identified and prioritized set of assets. You pivot to agency A’s EDR console and isolate 10 of the impacted devices. You dive deeper into the systems to confirm what you suspected – a Creepy Koala process has been run on the endpoints. You help the agency security operations center (SOC) prioritize their response to block the process, remove the bad files, and create rules within the EDR to block the process in the future. You work with your peers across CISA to distribute alerts and detection rules to all agencies. You now have what you need to render Creepy Koala effectively harmless against the entire federal government.
ECS + Elastic Deliver
Ultimately, Elastic-powered CDM dashboards empower incident responders like never before. With a broader and more enriched set of cyber-relevant data, coupled with a more unified approach to how we consume, manage, and analyze that data, our nation’s defenders can stop reacting to the problem and start being more proactive in defending their missions.