Automated Cyber Risk Intelligence
The National Vulnerabilities Database identifies over 3,000 new cyber vulnerabilities and exposures each month. How can your team prioritize cyber risk and focus your resources on the most pressing cyber threats? How do you determine which threats require immediate action and which can be scheduled for triage later?
Meet ECS Pathfinder
A Modular Platform for Targeted Cyber Defense
SaaS | On-prem | Air-gap Capable Delivery
With additional modules being added continually, ECS Pathfinder offers a buy-what-you-need model to ensure your organization can leverage the capabilities required to meet your unique needs and challenges.
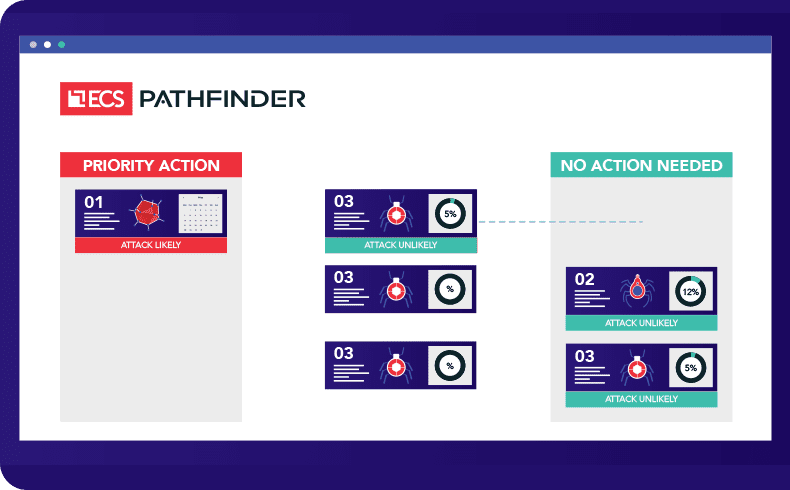
1. ECS Pathfinder Risk
Predict and Prioritize Exploitable Vulnerabilities
ECS Pathfinder Risk analyzes known vulnerabilities (CVEs) and leverages intelligence feeds to predict when and how they will be exploited.
- Stay Ahead of Exploits: Use AI to anticipate how and when vulnerabilities will be targeted.
- See Risk Over Time: Visualize vulnerability life cycles to guide patching and planning.
- Focus Resources Where It Counts: Prioritize CVEs by likelihood of exploit, not just volume.
- Accelerate Analysis: Quickly search and filter vulnerability data to zero in on what’s actionable.
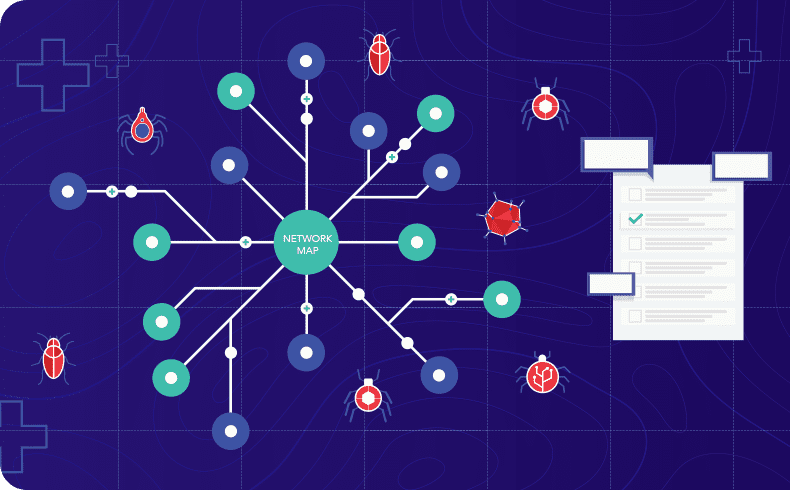
2. ECS Pathfinder Cartographer
Visualize and Protect Your Network in Real Time
Understanding your network is key to defending it. ECS Pathfinder Cartographer provides an interactive, real-time network map enriched with predictive exploit data.
- Map Risk in Real Time: See your network like an attacker would—complete with predicted attack paths.
- Scale with Confidence: Monitor millions of endpoints without losing performance or visibility.
- Get Answers Fast: Search and segment network nodes to surface the intelligence that matters most.
3. ECS Pathfinder Evoke
Extract Actionable Intelligence from Complex Data
ECS Pathfinder Evoke harnesses AI to identify entities, relationships, and cyber risks within intelligence reports and operational data, allowing the seamless analysis of unstructured data and the integration of that data into graph structures.
- Connect the Dots Faster: Automatically link intelligence, vulnerabilities, and infrastructure to surface hidden risks and critical dependencies.
- Boost Analyst Impact: Enhance machine-detected insights with expert-driven refinement to improve accuracy and relevance.
- Ask, Answer, Act: Use a conversational chatbot interface to rapidly query complex data and surface clear, actionable intelligence.
4. ECS Pathfinder Terrain
Contextualize Cyber Threats Through Organizational Impact
ECS Pathfinder Terrain maps organizational and operational data to cyber threats and asset information—enabling teams to understand the potential impact of threats within their specific mission environment. By aligning risk to organizational context, Terrain helps leaders prioritize response based on what matters most.
- Clarify Impact Quickly: Associate threats with operational functions and mission-critical assets to understand how cyber events could disrupt your organization.
- Support Informed Decisions: Turn fragmented threat data into mission-relevant insights that support prioritization and action.
- Build Shared Awareness: Provide a common operational picture that links cyber risk to business and mission outcomes across teams.
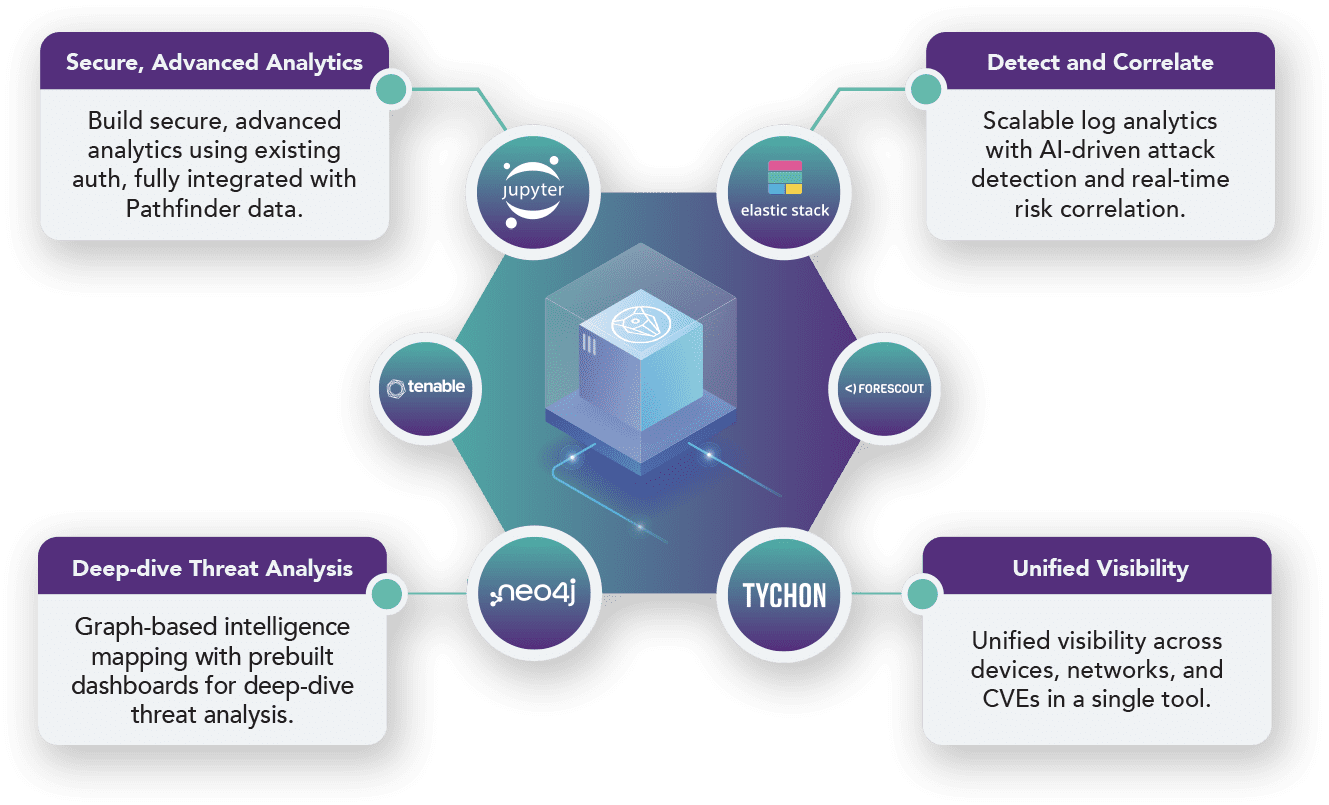
Seamless Integration with Cyber Analytics Tools
ECS Pathfinder integrates with industry-leading technologies to enhance your cybersecurity operations:
Big Bang Deployment: Scalable and Secure
ECS Pathfinder is deployed using the hardened Kubernetes framework and the DoD’s Big Bang framework, ensuring a secure, scalable, and rapidly accreditable cyber solution.

Deploy Anywhere, Securely: Run in the cloud, on-prem, or even air-gapped—your mission, your rules.
Move Fast, Stay Compliant: Accelerate ATO with hardened, accredited deployment frameworks.
Adapt on Demand: Scale fluidly with evolving mission needs, ensuring resilient cyber defense at every stage.



