By Doug Miller
Cybersecurity Threat Analyst
ECS Intelligence received notification from our Security Operations Center (SOC) that a spear-phishing email was sent to one of our customers with the following details:
From: <REDACTED> “lT Departmenrt” <REDACTED>
To: <REDACTED>
Subject: <REDACTED> Pending Case id:6831
Date: May 04, 2020, 12:09 PM HDT
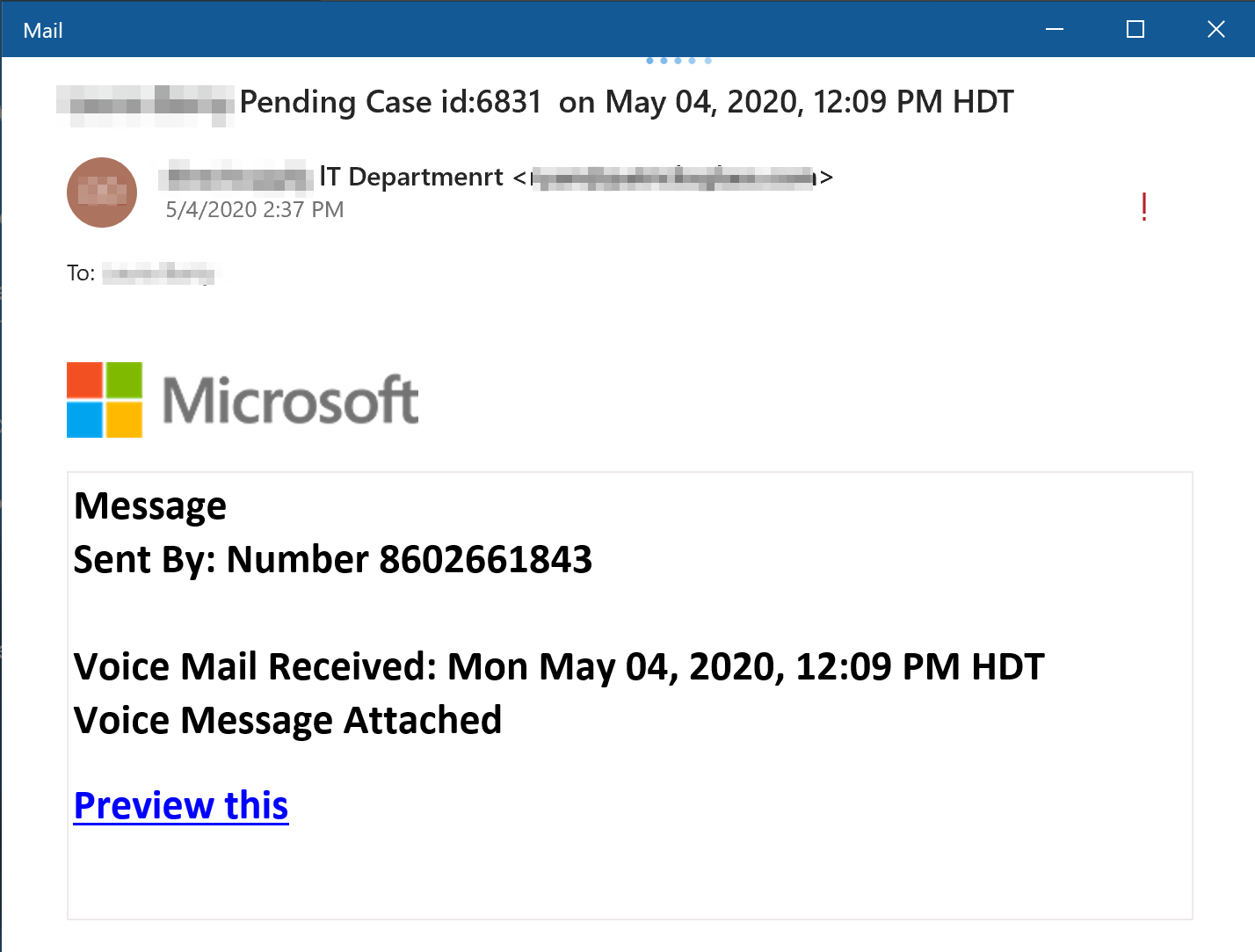
The email contained the following malicious link that will redirect the user to a compromised domain in which it will attempt to steal the user’s credentials:
hxxps://redirect.viglink.com?key=8e46920721cdfe7bc3f0d22c59660f74&u=https%3A%2F%2Fstage.<REDACTED>.org%2Fwp-admin%2Foffice%2F%23<REDACTED>@<REDACTED>.com&opt=true
Parsed URI
URL: https://<REDACTED>.org/wp-admin/office/#<REDACTED>@<REDACTED>.com
Redirect Tracking ID: 8e46920721cdfe7bc3f0d22c59660f74
This link redirects to the website of an energy company—a legitimate site that was compromised by the attacker, who implemented a framework designed to steal the targeted user’s credentials. The script is dynamically generated upon load with a custom four-digit RC4 symmetric encryption key stored in an array. The script is Base64 encoded, then RC4 encrypted, then Base64 encoded again. The key also changes with each dynamically generated script. The embedded script is static and at the time of analysis, was configured with the following values:
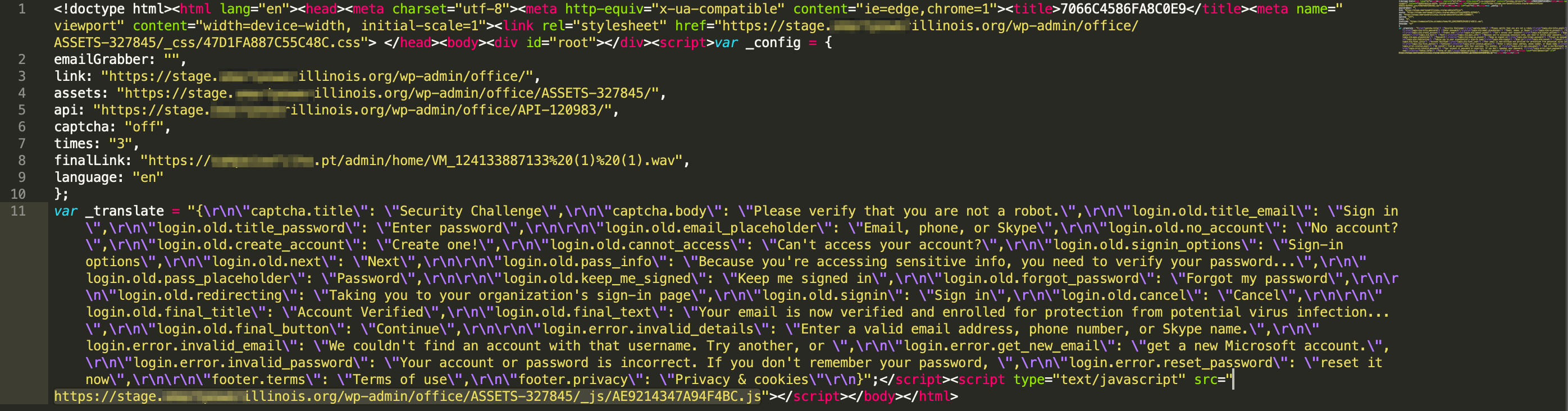
var _config =
{
emailGrabber: “”,
link: “https://stage..org/wp-admin/office/”,
assets: “https://stage..org/wp-admin/office/ASSETS-327845/”,
api: “https://stage..org/wp-admin/office/API-120983/”,
captcha: “off”,
times: “3”,
finalLink: “https://.pt/admin/home/VM_124133887133%20(1)%20(1).wav”,
language: “en”
};
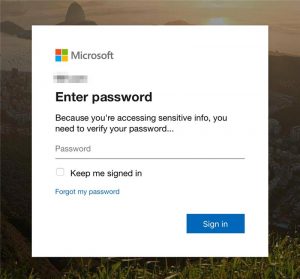 The underlying framework is built on ReactJS, and convincingly replicates the Office365 login and redirect.
The underlying framework is built on ReactJS, and convincingly replicates the Office365 login and redirect.
The credential stealer is designed to give the victim three password attempts, after which it will present the user with a “valid” login and redirect to another compromised website that contains a 13-second audio recording (a fake voicemail message mentioned in the initial email). This audio recording has been analyzed and does not appear to contain any malicious code. As with the energy company, this compromised website runs on WordPress. In these cases, as well as the compromised website of the initial email sender, the attacker likely targeted the same vulnerabilities in each domain.
https://<REDACTED>.pt/admin/home/VM_124133887133%20(1)%20(1).wav
In this instance, the attack appeared to target only the user’s credentials and not their host machine. This framework is modular, however, and it would be trivial for the attacker to replace the final link with a malicious payload.
ECS’ experts deconstructed this spear-phishing attack to better understand and protect against these threats. Learn more about our cybersecurity solutions and Cyber Center of Excellence.
Ready to take part in the fight against cyberattacks? Learn more about cyber careers at ECS.