By Dave Howard
Director, Security Operations
The ever-expanding cyber threat landscape is driving an increasing volume of cyberattacks, as malicious actors search for new opportunities to exploit vulnerabilities across organizations’ environments. Of the many tactics used by these actors, phishing is among the most common, in which a group of victims are targeted by fraudulent messages—emails, phone calls, and the like—designed to steal sensitive information. A related technique, spear-phishing, involves targeting a specific individual, often with the use of personal information to increase the likelihood of a successful attack. These spear-phishing attacks have been known to target all levels of an organization, including chief information security officers and other C-suite executives.
ECS Intelligence was alerted to one such attempt, in which one of our customers was targeted with an email containing a malicious link. Investigation into this attack revealed a complex scheme, including an accurate emulation of the Microsoft 365 login portal, a fraudulent voicemail, and triangulation between three legitimate websites that had all been compromised by the attacker.
The Attack
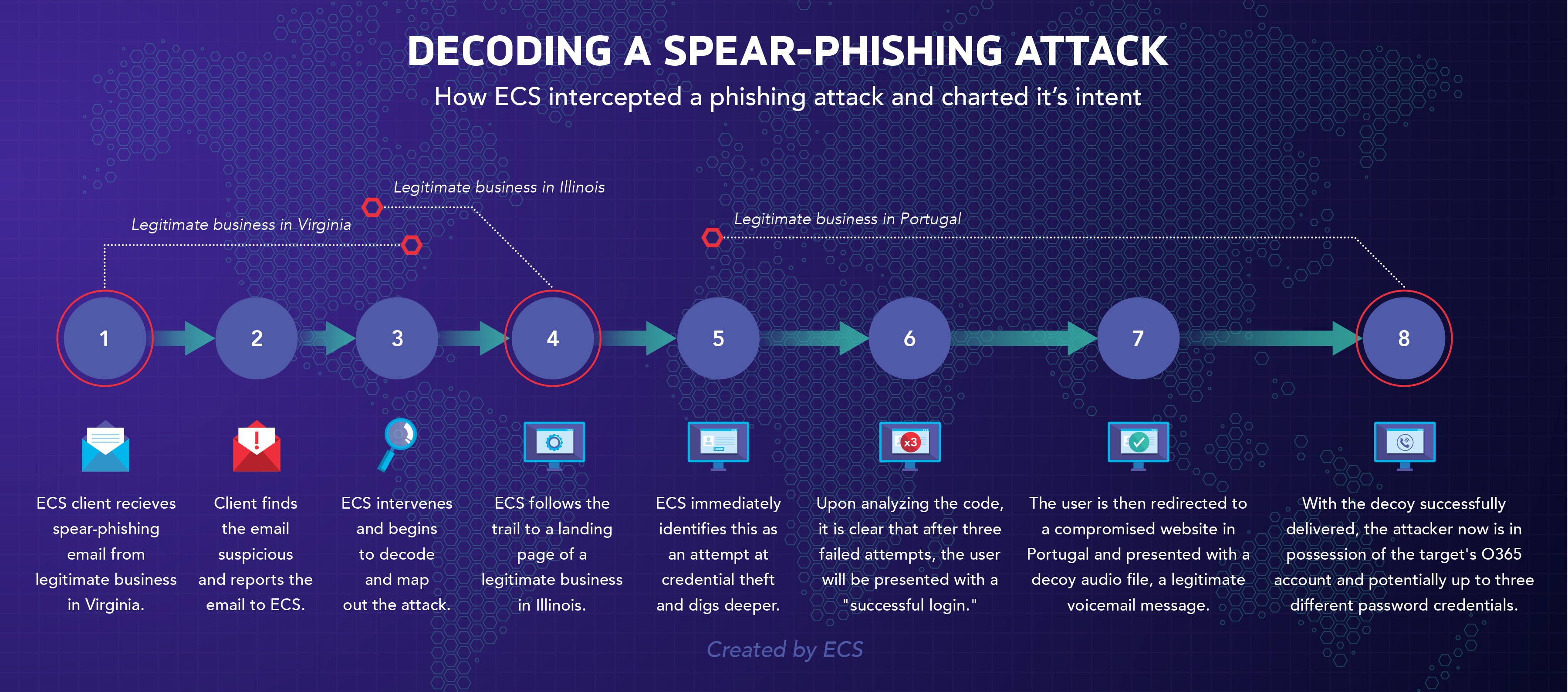
An ECS customer received a fraudulent email ostensibly from the IT department of a Virginia-based manufacturing company. The email was clearly targeted. Its subject line contained the customer’s first and last name, indicating that the attacker may have been using a leaked database of names and emails to automate the delivery of these phishes. The email was also nearly flawless, but for a single typo, in which “IT Department” was misspelled as “IT Departmenrt.” In this case, the typo was enough to alert the intended victim that something was amiss. She flagged the email as suspicious and the attack went no further, at which point ECS Intelligence began to investigate.
The initial email, which lured the target with the promise of a voicemail recording, contained a link redirecting the user to a landing page within the website of a legitimate business—not the Virginia-based manufacturing company, but an energy company in Illinois. This website contained a malicious script designed to steal the victim’s email and password through a fraudulent Microsoft 365 login portal, accurate down to the background and subtle animations. After three password attempts, this portal presented the user with a “valid” login, redirecting them to a third website based in Portugal containing a 13-second audio recording—the fake voicemail. This audio has been analyzed and does not appear to contain any malicious code.
All three compromised websites ran on WordPress, which indicates that the attacker exploited the same known vulnerability in each case. While this attempt appears to have only targeted the user’s credentials, it would have been trivial for the attacker to replace the final link with a malicious payload targeting the user’s host machine.
Key Takeaways
The ECS Cyber Center of Excellence combines best practices, technology, and thought leadership to deliver state-of-the-art cybersecurity solutions. Learn more about how we can protect your organization.