As we have seen with security breaches in recent years – including the SolarWinds attack – it can be challenging for federal security leaders to effectively detect cyber threats across their networks. In the last few decades, private-sector organizations have established tools to help monitor for malicious activity, but until recently, the federal government hasn’t had one centralized method.
The Continuous Diagnostics and Mitigation (CDM) program standardizes how civilian agencies monitor their networks for cyber threats while improving their cybersecurity postures. The program operates under the direction of the Cybersecurity and Infrastructure Security Agency (CISA).
Through this centralized strategy, the CDM dashboard empowers an ideal threat-hunting environment for cybersecurity professionals to identify threats before they strike. DHS is leading the way in exploring advanced endpoint detection and response technologies available to the agency personnel that need them.

The May 2021 release of the Executive Order on Improving the Nation’s Cybersecurity greatly accelerated these efforts. The order requires agencies to deploy an endpoint detection and response (EDR) capability. CISA is tasked with leading the Federal EDR deployment initiative to support host-level visibility, attribution, and response regarding Federal Civilian Executive Branch (FCEB) information systems at scale. The order also mandates the authorization of much-anticipated changes to the agreements between FCEB agencies and DHS, which now require agencies to share detailed information about their systems through the CDM program.
For the first time, the CDM program now has both the technical ability to hunt for threats at scale and policy authorizing it to do so.
Here’s how federal cyber professionals can leverage these updates and make the most out of the CDM program:
Standardization Makes it Possible to Hunt at Scale
Until now, the lack of normalized data formats has contributed to poor data quality and made it challenging to identify potential vulnerabilities at scale. Open technology tools and common schema specifications hold the power to unlock previously disparate data.
The CDM dashboard maximizes common schema tools. Increased support for the dashboard means data from various sources, locations, and formats can be more quickly synced and analyzed.
Under the Chief Financial Officers (CFO) Act, there are 23 agency-specific dashboards that feed into the wide-spanning federal CDM dashboard, as well as data from more than 70 non-CFO Act agencies. CISA Analysts can query all of the Agency dashboards at once, to identify the prevalence of vulnerabilities and at-risk systems across the entire FCEB. As even more agencies adopt the centralized CDM dashboard, the amount of valuable intelligence will continue to grow, delivering the comprehensive government-wide threat visibility required to combat increasingly sophisticated cybercriminals.
Finding Hidden Threats Quickly Depends on Data
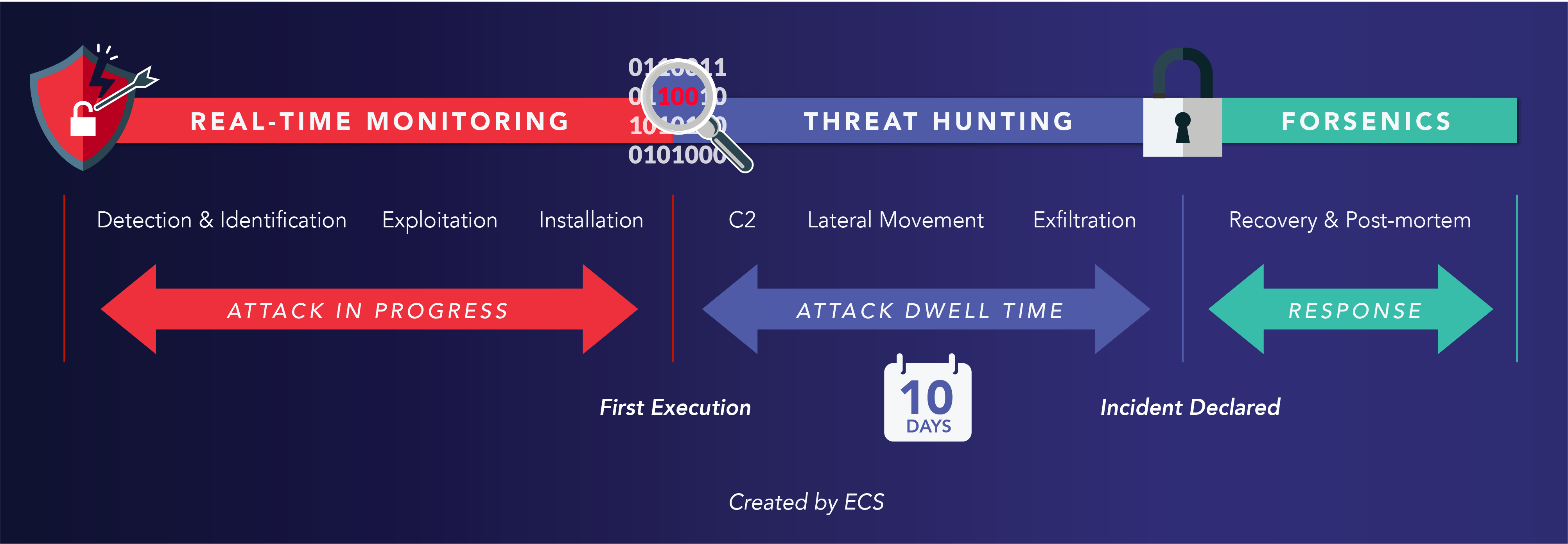
Successful threat hunting begins with having the right data to answer the right questions at the right time. Without that data, there is no hunt. Why? Because dwell time – the time between when a compromise first occurs and when it is detected – is on the rise.
Sophisticated state-sponsored threat actors can remain undetected for months; foreign adversaries’ average dwell time is 10-plus days, and in the SolarWinds case we saw dwell times of 300-plus days. The only way to accurately analyze these long dwell times is to retain telemetry for longer periods of time so that historical analysis can be performed.
Data consolidation opens up more insights that can be gathered quickly and cost effectively. While this is good for threat hunters – the more data you have, the more effective your threat hunting process will be – it can easily overwhelm agency systems with its sheer volume and velocity. Further, some degree of data normalization is necessary to enable automated detection at scale and to help analysts find what they’re looking for. The CDM dashboard provides a model for government-wide data normalization and helps analysts search through mountains of data – fast. More data means determining where a breach occurred, what it impacted, and how it might be related to other events.
From Reactive to Proactive Cybersecurity
Agencies need an offensive mindset in today’s security environment and must always assume they’re at risk of being compromised. It’s in this zero-trust world where threat hunters can play a critical role. They understand where and how to look for security threats and can analyze the trends the CDM dashboard generates. Threat hunters are prepared to “fight the network” to eradicate adversaries from within ever-expanding agency perimeters.
It’s not a matter of if, but when the next cyberattack occurs. When we started writing this article, the Microsoft Exchange breach “Hafnium” was discovered; by the time this article is published, the next big breach – or several big breaches – will have already taken place.
With a more unified approach to how we consume, manage, and analyze data, the nation’s defenders can stop observing the problem and start playing offense, making CDM’s government-wide vision of proactive security a reality of our cyber defense.
The effort has gained significant support from policymakers as well. Last year, the National Defense Authorization Act (NDAA) gave CISA the ability to collect data from federal agency networks and proactively hunt for vulnerabilities without notifying the individual agencies. The Executive Order on Improving the Nation’s Cybersecurity contains dozens of new and enhanced provisions which provide CISA with the authority to make a significant impact. In order to maintain transparency across government, DHS will be required to report the findings of this proactive threat hunting to Congress. With the CDM dashboard, this information is easily shareable, but adhering to the NDAA while continuing to increase threat hunting efforts requires agencies to change the way data is stored, accessed, and analyzed.
In its continuous evolution, more features will be added to the CDM dashboard during the government’s next fiscal year. Updated capabilities are already being piloted at a handful of smaller agencies to measure potential impact. These enhancements include a CDM-enabled threat hunting capability, which pulls log data into the agency dashboard and enables queries across agencies from the federal dashboard to proactively search for threat activity. Generating deeper insights from across the government to alert threat hunters is a giant step forward, and the CDM dashboards can enable this – identifying threats in time to make a difference.