Leveraging AI toMaximize Cyber Insights
The National Vulnerabilities Database identifies over 3,000 new cyber vulnerabilities and exposures each month. How can your team prioritize cyber risk and focus your resources on the most pressing cyber threats? How do you determine which threats require immediate action and which can be scheduled for triage later?
MEET PATHFINDER
ECS PATHFINDER CORE
Leverage Your Data. Predict Your Future.
Is the data you generate and the intelligence you gather staying siloed? ECS Pathfinder, a holistic cyber visibility platform that drives operational intelligence, leverages your data to generate useful insights across the enterprise.
Minimize time spent in patch cycles. Maximize applicable areas for your intel sources. Let your blue team focus on what they do best.
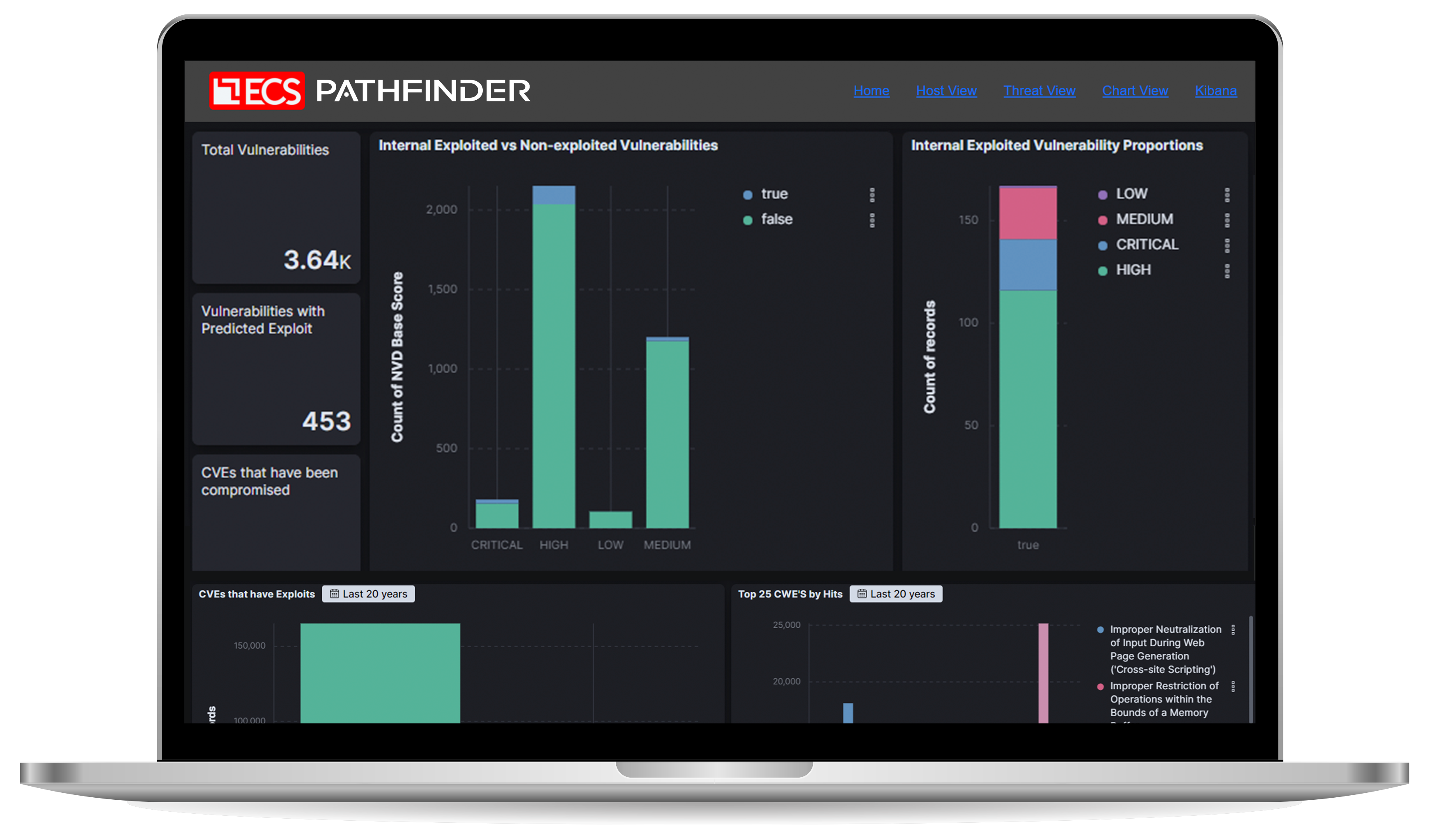
Prioritize vulnerabilities by attack probability, risk, and urgency.
- Determine the real-world exploitation timeframe of vulnerabilities to clearly assess the cyber risk landscape.
- Achieve a lower risk environment by expending resources where they matter most.
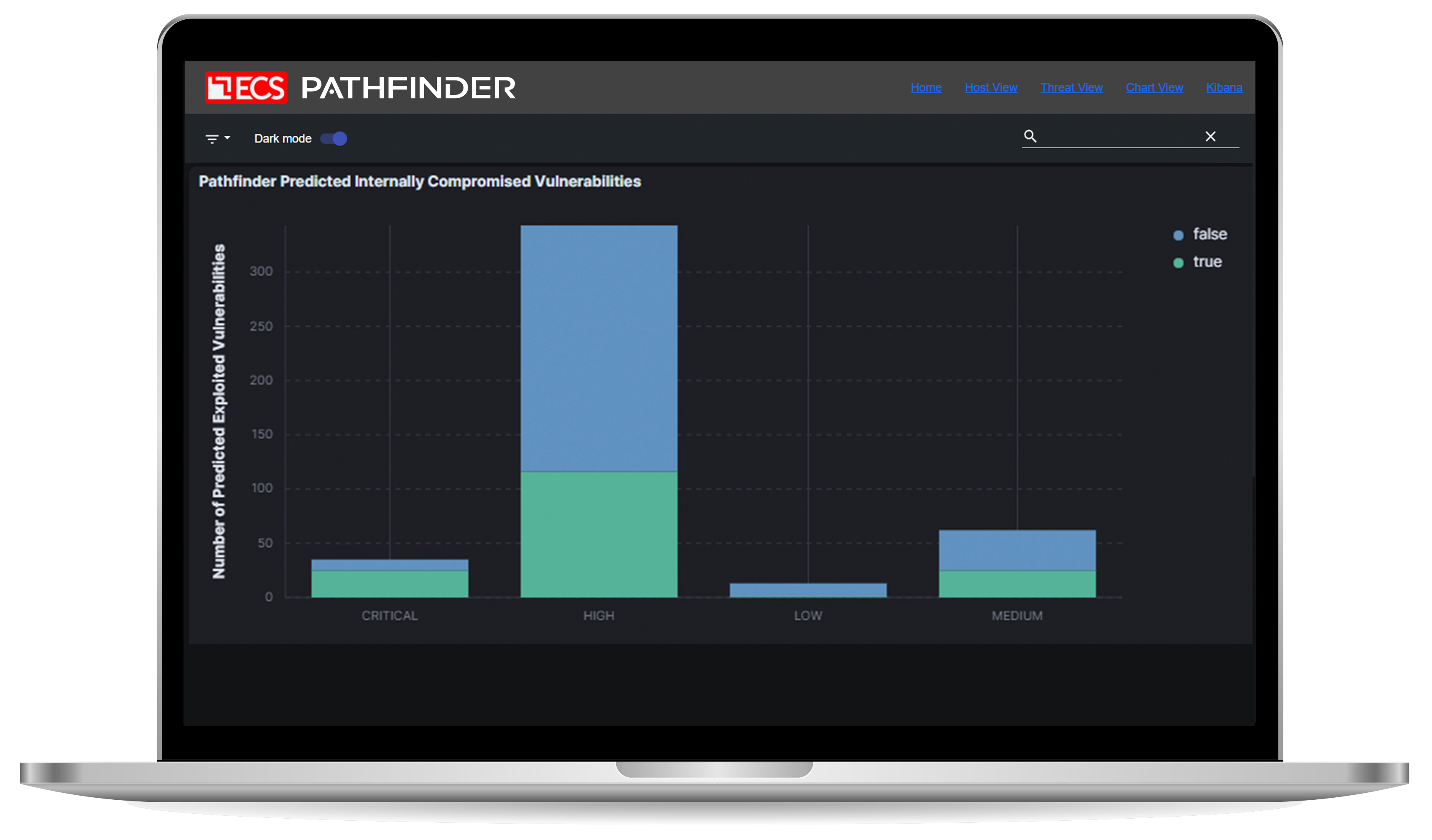
Use AI to predict when attackers will strike.
- Use threat intelligence and data-backed time windows to plan vulnerability patching timelines.
- Force your adversaries to spend increasing amounts of effort to achieve marginal outcomes.
- Achieve a lower risk environment by expending resources where they matter most.
Increase the value of every dollar spent on cybersecurity.
- Use vulnerability intelligence to assess critical applications, build smarter POAMs, and eliminate wasted resources.
- Reduce the need for expensive incident response and triage and lower your cyber insurance costs.
- Achieve a lower risk environment by expending resources where they matter most.
ECS PATHFINDERCARTOGRAPHER
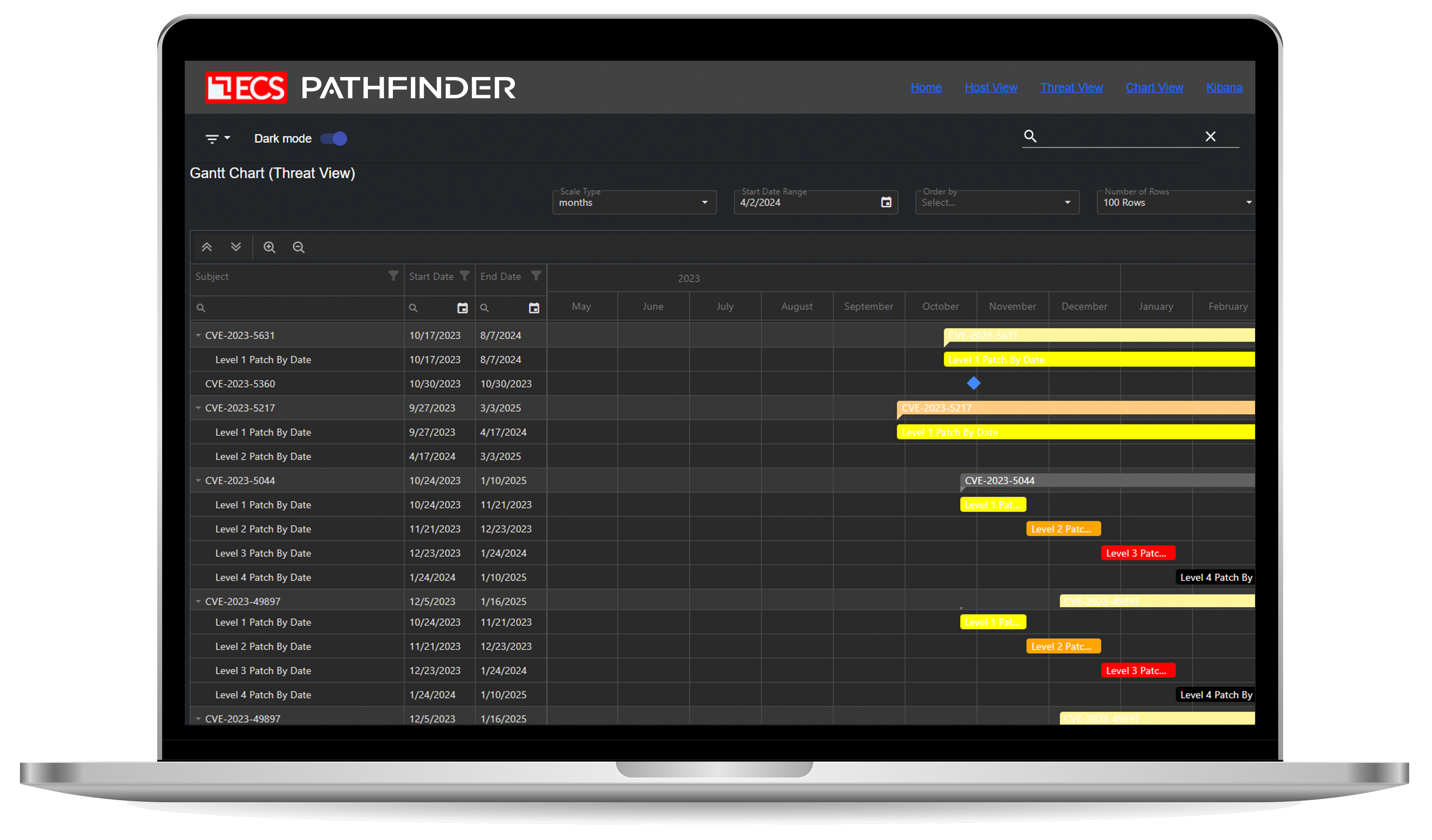
Sprawling, complex networks are difficult to understand and visualize. If you don’t know your network well, you’re not well-positioned to identify and understand vulnerabilities, prevent intrusions, or respond effectively when intrusions occur.
ECS Pathfinder Cartographer leverages AI to:
- Produce an interactive visualization of your network, including a heat map that reveals the locations of high-threat vulnerabilities.
- Help you understand the location of a compromise — actual or predicted — as well as likely attack paths through your network.

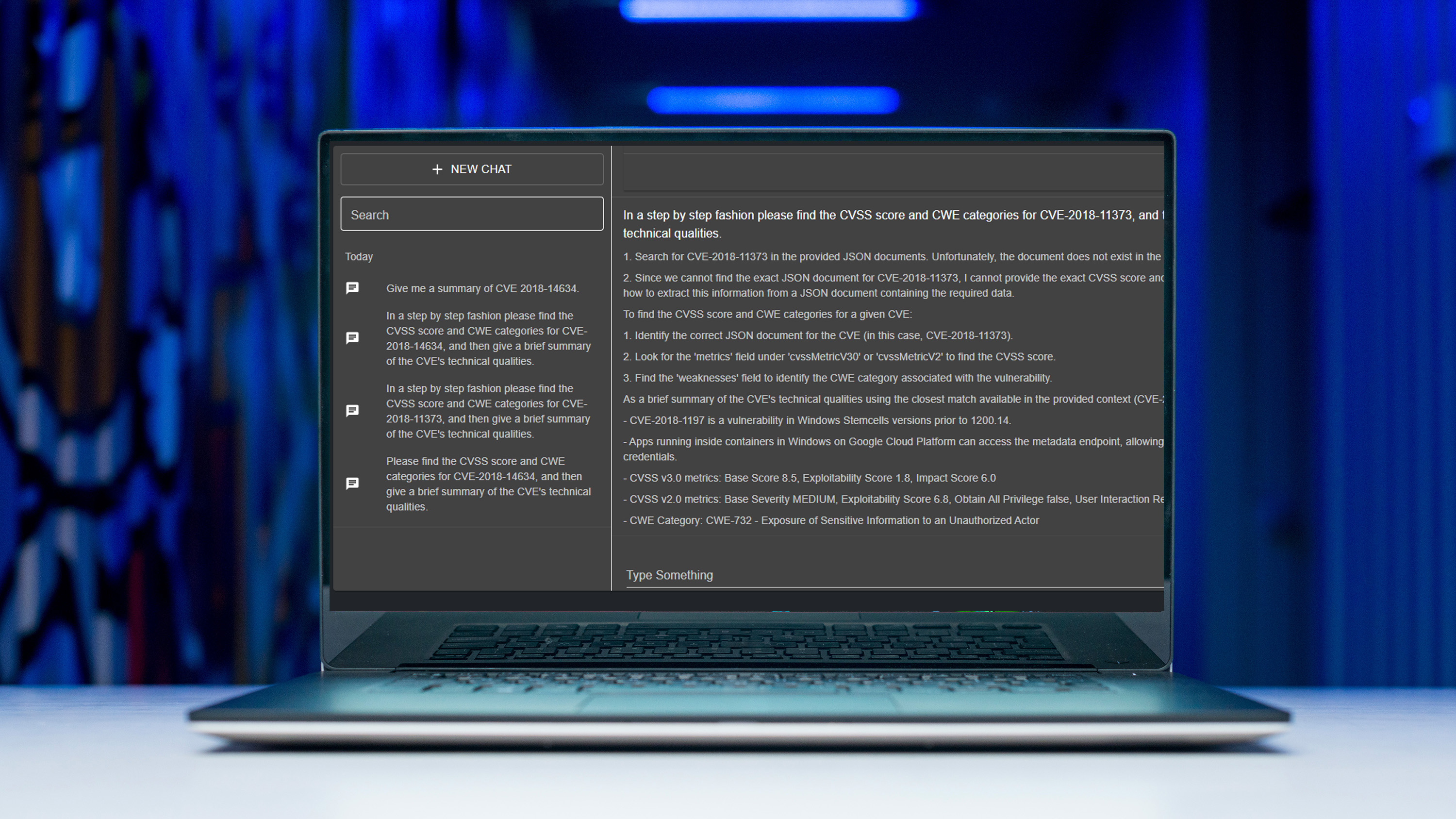
ECS PATHFINDER EVOKE
Enterprise organizations often collect and generate more data and intelligence than they can analyze and use.
ECS Pathfinder Evoke leverages machine intelligence, entity and relationship recognition, and a set of custom-developed ontologies to:
- Extract meaning and make connections a human analyst might miss, at the speed of silicon.
- Apply both internally generated and externally collected intel to your organization’s mission, providing critical insights to inform critical decisions.
A MODULAR PLATFORM WITH FLEXIBLE DELIVERY MODELS
With additional modules being added all the time, Pathfinder offers a buy-what-you-need model to ensure your organization can leverage the capabilities required to meet your unique needs and challenges.

SaaS

On-premises