Making Smart Cities Cyber Smart
Smart devices dominate our pockets, workspaces, and homes, and they don’t stop there. Our cities are integrating smart technologies to make life ever easier for their inhabitants. From the infrastructure on up, smart cities leverage new technology to improve operations, connect with residents, and promote local economies. With sensors, transmitters, and devices communicating with one another, smart cities can even optimize energy distribution, increase public works efficiency, and improve air quality.
The concept of a smart city is not brand new. In 1974, Los Angeles was the first urban area to kickstart the smart city movement by creating the first urban big data project. Twenty years later, Amsterdam created a virtual digital city to promote the use of the internet in 1994. As the smart city and infrastructure movement accelerated in the mid-2000s, Cisco and IBM launched comprehensive research programs that developed solutions to urbanization challenges, introducing the smart city concept as we know it today.
Cybersecurity in Smart Cities
Sensors, security cameras, and transmitters throughout a smart city act the same as any Internet of Things (IoT) devices. These devices collect data from their environments, which is transmitted back to systems and hubs to inform decision makers, just like an Apple watch transmits information to an iPhone after a workout. The same cybersecurity risks that we see at home apply to smart cities and infrastructure on a much larger scale, as the consequences of a breach on an entire city system are potentially catastrophic. As the Wall Street Journal puts it, the potential for harm in a compromised smart city is endless.

To better understand the risks and rewards of smart cities and connected infrastructure, we spoke with Josh Salmanson, ECS chief architect and vice president. Josh has been building enterprise IT systems for the last 25 years across the commercial and government spaces. Josh also has experience providing security solutions for more than half of the sixteen critical infrastructure sectors defined by DHS.
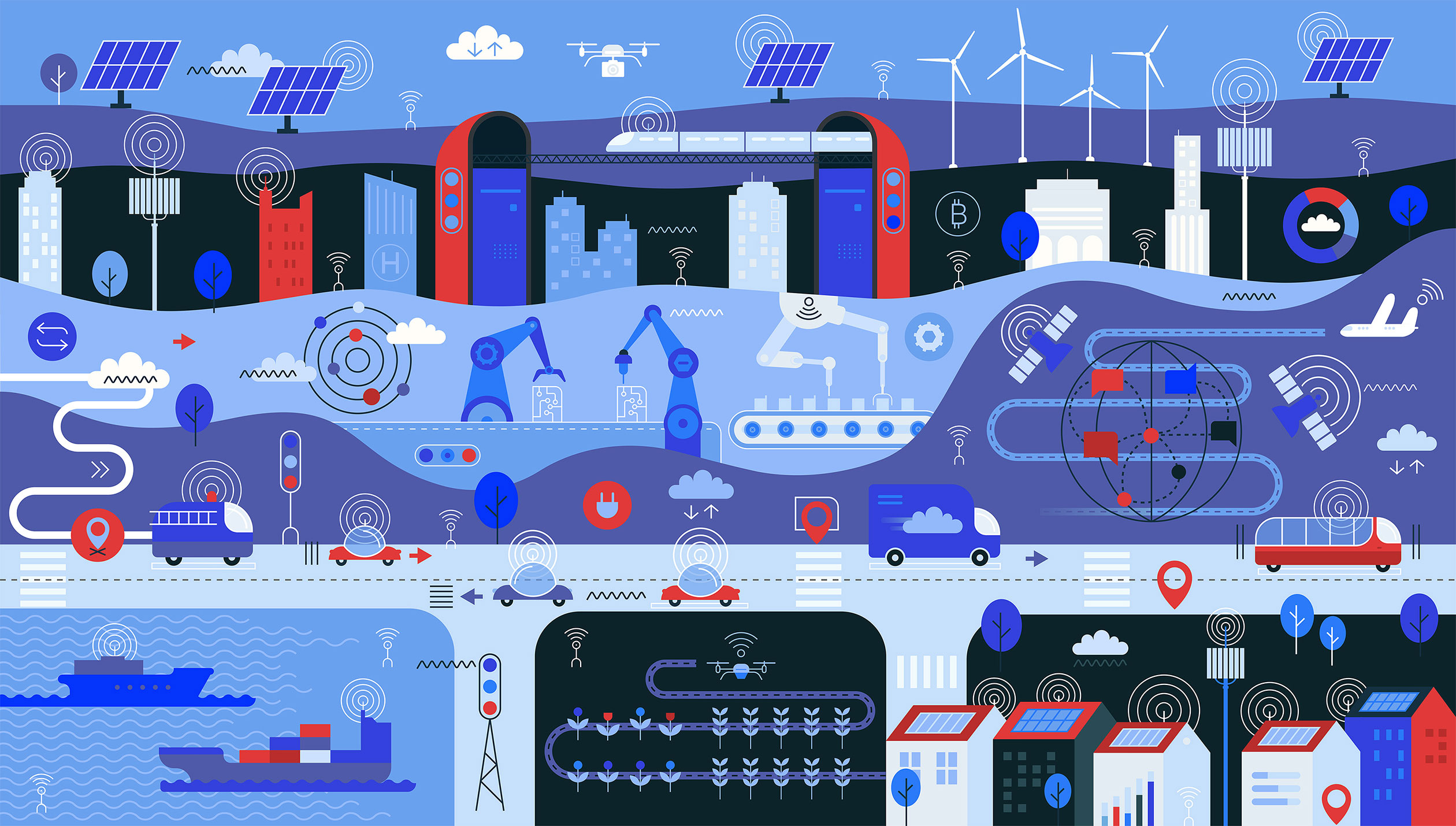
How do smart cities and connected infrastructure impact our day-to-day lives?

The pieces of connected infrastructure that make up our smart cities are designed for operational efficiency, streamlining integration across and within different services sectors. This level of integration provides city managers with a comprehensive view of their cities, empowering them to manage everything from small inconveniences to major crises.
Connected infrastructure is designed to make your life as a resident much more convenient. For example, integrating traffic, transportation, and communications systems can inform commuters on predicted travel times, traffic, and other options before traveling. Smart cities also make infrastructure safer by providing much better data to inform decisions regarding maintenance activities. This helps smart cities avoid outages by prestaging key components ahead of power failures.
Smart cities were designed to ease management and simplify integrated operations, taking an enterprise view. The recent proliferation of IoT-based solutions are now coming into the mix both at home and at work. These impacts can be both positive and negative.
What kind of security concerns do these systems present?

Many of these systems were built on what people believed to be private networks and hidden protocols, which are not really hidden at all. In practice, this increased technical risk is often at odds with business cost drivers and several decades of focus on operating margins.
Many businesses have unknowingly made decisions that have led to unintended consequences. For example, it’s expensive to send staff out to inspect remote sites to monitor and maintain their systems. Many vendors would place inexpensive Wi-Fi devices on the operational network for this purpose, often without telling their customer and without fully understanding the risk. Sometimes, these systems, which were designed to be isolated, were also connected to enterprise networks under the assumption that they would be better protected by corporate security. The corporate enterprise monitoring systems, however, often did not see the operational technology systems and protocols or understand how to distinguish between typical activity and an adversary action. These actions put safety-focused systems directly on corporate and public networks, creating a back door for bad actors to access the critical systems and often the rest of the enterprise. Although these back doors have been exploited in the past and will continue to be exploited in the future, secure architecture methods have emerged to better achieve safety and business objectives.
The impact of a bad actor accessing these systems could be anything from an inconvenience to a life-threatening sequence of events. Take, for example, a scenario in which a bad actor accessed a water treatment plant’s system. If that bad actor decided to exploit this access point, they could apply ransomware, shutting off the water until a ransom is paid. They could disable sensors and release untreated water into the water supply. Depending on their capabilities, they could destroy the system altogether.
Many IoT-based systems connect directly to the internet, either by Wi-Fi or built-in telecommunications capability. Combined with typically lax consumer network security, this opens up many privacy, safety, and security issues—especially now, with the pandemic forcing people to connect from their unsecured home networks to business networks, which magnifies the attack surface exponentially.
What is the right approach to integrate cybersecurity into these systems?

Implementing security protocols into existing smart city infrastructure can be a huge challenge because when these cities were created, security was not front-of-mind. There has been a consistent effort over the last half decade to design security solutions that better protect, detect, and recover adversary activity on legacy systems.
In areas like the national power grid, the government has made a huge effort to support a commercial—but regulated—industry to enhance the grid’s security and resilience. Other sectors are making improvements but are working at different cadences. These problems are hard to solve, expensive to fix, and often cannot be replaced. You can’t swap out a dam or a city’s hundred-year-old sewer system or rapidly build another in parallel. Progress is being made through collaboration, innovation, legislation, and policy and is occasionally accelerated by events and action on similar infrastructure across the globe.
The Department of Homeland Security (DHS) has identified sixteen critical infrastructure sector verticals. Those sixteen sectors and their industry partners work together to improve sector security posture. Through sector-specific peer collaboration, member-driven nonprofit organizations like the Information Sharing and Analysis Centers (ISACs) help members share sector-specific security threat intelligence and mitigation strategies for owners, operators, and stakeholders. This helps increase assurance in current and future infrastructures. Legacy systems can be made more secure and new systems can be engineered and built for resilience.
What is the future of smart cities and infrastructure?

In the future, smart cities need to adopt more resilient architectures. As new smart cities are built, existing cities are modernized, and capabilities are expanded, they must include robust cybersecurity architecture, engineering, and operations right from the start. In the long run, taking the time to create strong, secure, resilient infrastructure will protect residents from myriad security threats, be they minor intrusions or catastrophic system failures.
ECS currently supports multiple ISACs. Our commercial managed security service provider (MSSP) practice is helping customers in several sectors secure their critical infrastructure. If your organization wants total visibility into all network endpoints, schedule a meeting with our cybersecurity experts today.





