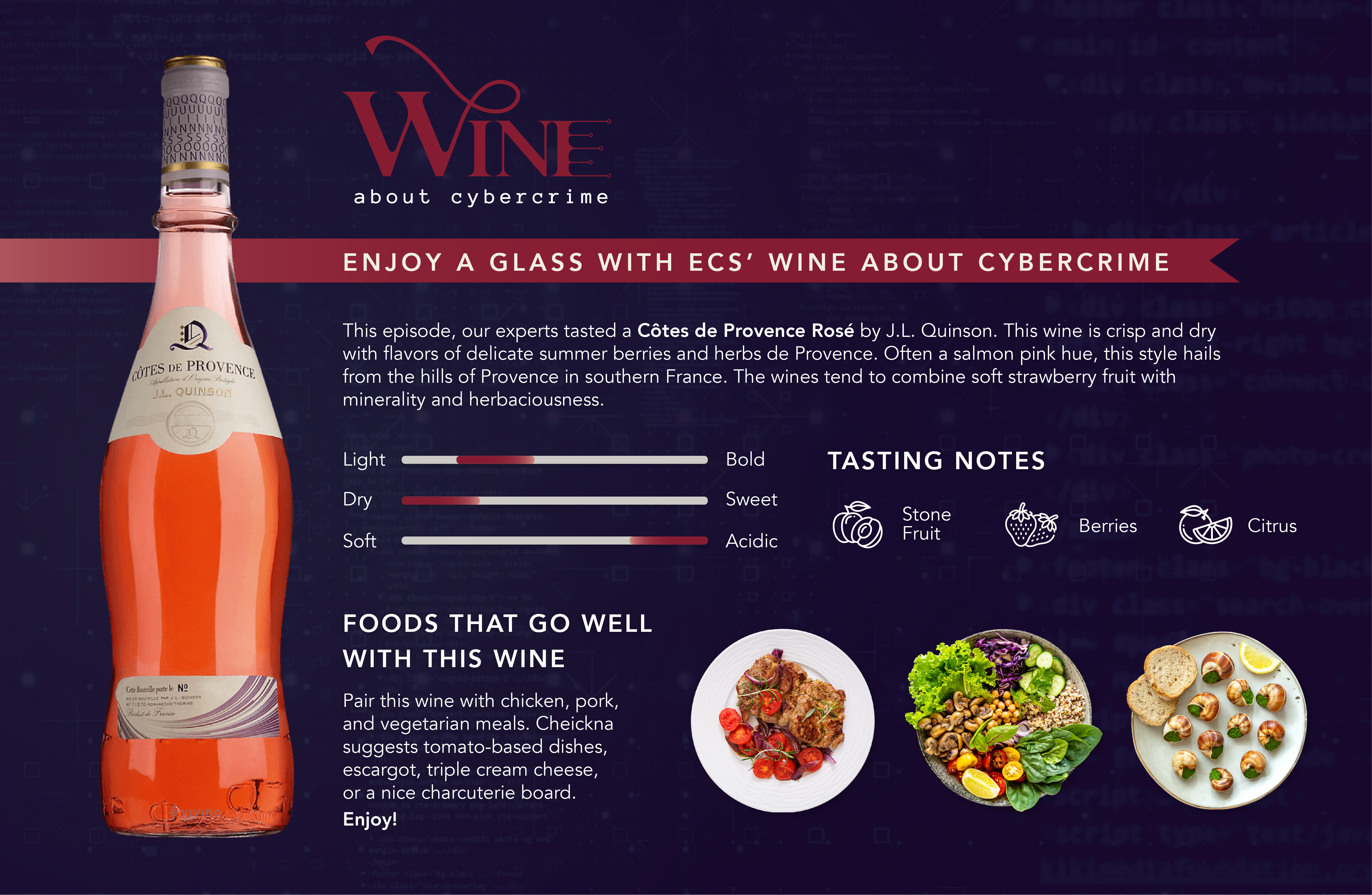
Cybercrime is no chilled glass of Sauvignon blanc
on a hot summer’s day.
Wine About Cybercrime is a cybersecurity podcast where we invite cyber experts to take a break, enjoy some wine, and discuss the latest challenges and pain points in the field.