When a global hospitality company spun off from its parent organization, the company was left to build its cybersecurity processes from scratch. With no access to previous cybersecurity systems and resources, and only a three-person information security team, the company sought a vendor-partner to create a new solution from the ground up.
Building a Comprehensive Solution
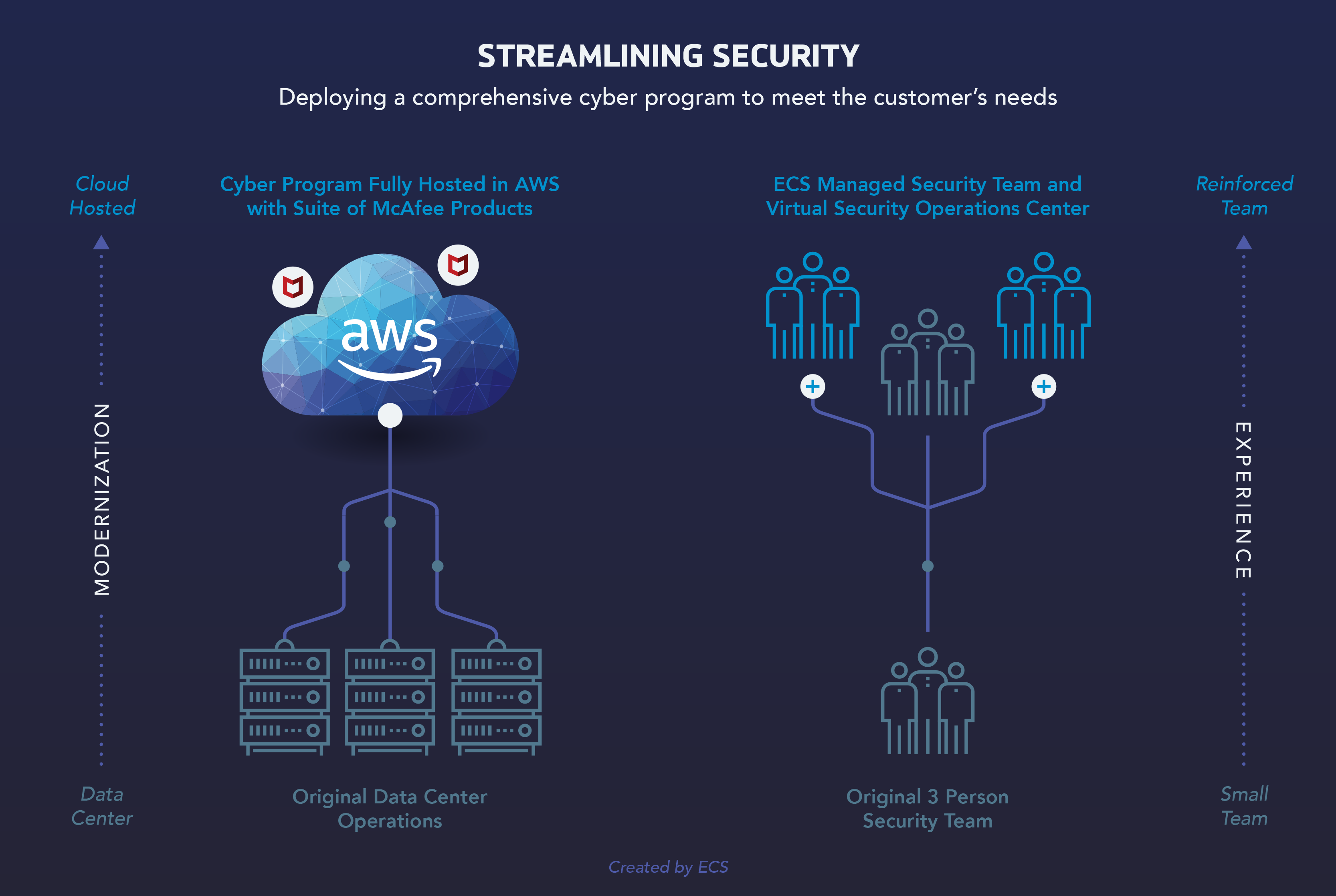
The company engaged ECS to design and implement its cybersecurity system with several specific goals in mind. Because of their small cybersecurity team—a chief information security officer (CISO) and two system administrators—they wanted a partner to scale their organization with trained, experienced personnel providing cybersecurity as a managed service. At the same time, they wanted to scale down their data center operations in favor of staffed, hosted technology.
ECS worked closely with the company’s leadership to build a system that meets these objectives. After several months of collaborative planning, ECS deployed a comprehensive cyber program fully hosted in Amazon Web Services (AWS) and our colocated (colo) data center, co-managed by ECS personnel augmenting the client’s cybersecurity team. ECS’ multipronged solution provides endpoint security, network security, vulnerability management, data loss prevention, log management, and security operations through our virtual security operations center (SOC) and security information and event management (SIEM) platform.
Continuing Protection
Today, ECS provides a fully hosted, fully managed cybersecurity program, protecting the entire client organization, including critical assets in the cloud. ECS personnel use a suite of McAfee products to secure user endpoints, as well as network security devices to monitor for malicious web traffic, and data prevention strategies to protect against the exfiltration of personally identifiable information (PII), Payment Card Industry (PCI), and other sensitive data.
With a three-person information security team, the client relies on ECS to provide expert personnel and institute best practices in support of the overall cybersecurity solution. To that end, ECS creates runbooks, compilations of routine procedures and operations, for every scenario in which our team engages with the client, including day-to-day operations, change control processes, and incident response procedures. Through the interoperation of these experienced personnel—as well as the use of advanced technology and proven processes—the client’s lean information security team can successfully maintain and continuously improve their cybersecurity apparatus.




