By Scott Hoge
Vice President of Cybersecurity
The Problem: Security That Gets in the Way
For years, the trade-off around cybersecurity has been understood to be: if you want more security, you must accept less usability. Endless logins, constant MFA prompts, VPN friction, and session timeouts interrupt work, break concentration, and ultimately drive risky behavior like MFA fatigue and shadow IT.
The uncomfortable truth is this: if a zero trust implementation makes life harder for users, it’s already failing. Friction doesn’t just hurt productivity; it actively weakens security.
The Shift: From “Always Prompt” to “Always Assess”
Zero trust was meant to move us from “trust but verify” to “never trust, always verify.” But many organizations misinterpreted that mandate as “always challenge the user.”
Modern zero trust doesn’t mean more prompts. It means better decisions, made continuously, in real time, and mostly out of sight. The goal isn’t visible enforcement. The goal is invisible security that only surfaces when risk truly changes.
That’s where many programs stall and where ECS’ approach differs.
Invisible Zero Trust: What Actually Changes
Invisible zero trust shifts the burden of verification away from the user and onto the infrastructure. Instead of repeatedly asking users to prove who they are, systems continuously evaluate contextual trust signals in the background.
NIST SP 800-207 reinforces this model: access decisions should be dynamic, contextual, and based on multiple live attributes, not just a login event or static role.
In practice, that means evaluating trust continuously using signals such as:
- Device trust: Is the device managed? Patched? Running EDR? Known and healthy devices earn higher trust.
- User behavior analytics (UBA): Is this login consistent with normal behavior, time, and location?
- Network context: Is the user on a secure network or an untrusted public connection?
When these signals align, access is seamless. No interruptions. No prompts. Just work.
Security That Only Appears When Needed
The journey to invisible zero trust follows a simple progression:
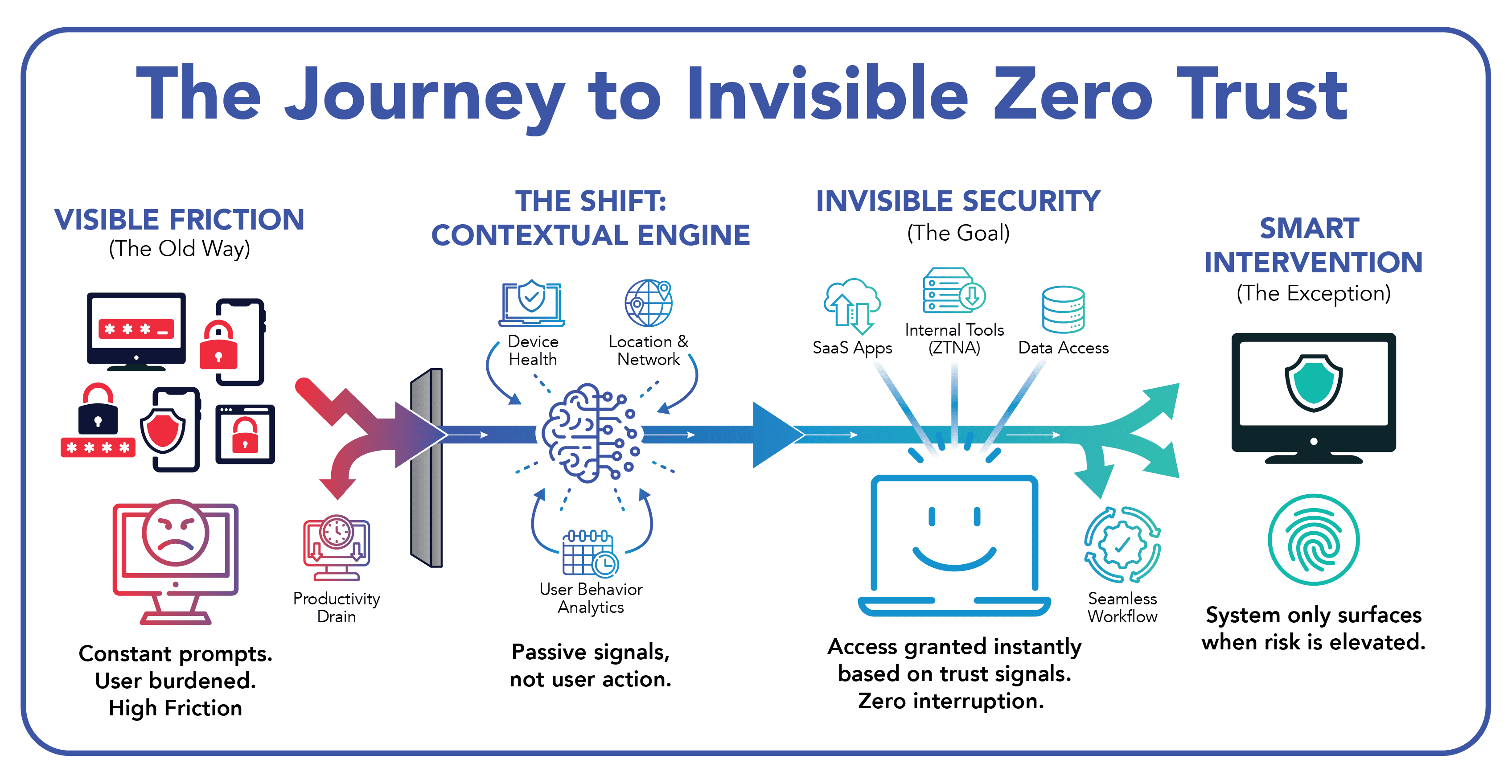
This model isn’t theoretical. It’s how mature zero trust environments operate.
The Building Blocks of Invisible Zero Trust
To get there, agencies need to look to move beyond legacy perimeter controls and static credentials. Three capabilities matter most:
1.
Continuous Adaptive Risk and Trust Assessment (CARTA)
Traditional security verifies trust once at login. Zero trust requires continuous evaluation throughout the session. If a device becomes compromised mid-session, access should immediately degrade or terminate without the user needing to click anything. Gartner formalized this concept as CARTA, and it’s foundational to invisible enforcement. foundational to invisible enforcement.
2.
Passwordless Authentication (FIDO2 / WebAuthn)
Passwords are the single biggest source of friction and one of the weakest security controls. Passwordless authentication replaces typed secrets with high-assurance signals like biometrics (Windows Hello, Touch ID) or hardware keys. When paired with a trusted device, authentication becomes both stronger and nearly invisible.
3.
The End of the Full-Tunnel VPN
Nothing disrupts workflows like launching a VPN just to access one internal app. Modern Zero Trust Network Access (ZTNA) enables per-application micro-tunnels, created automatically in the background when policy conditions are met. Users click the app and the connection just works.
In a mature zero trust environment, the user experience should flow as follows:
- An employee signs into their laptop with biometrics.
- SaaS apps open instantly with no passwords or MFA.
- Sensitive on-prem systems are accessed through silent, app-specific tunnels.
- Only when context changes — an unmanaged device, an unusual location — does security become visible with a step-up challenge.
Security is invisible 95 percent of the time and intentional the remaining 5 percent.
Usability is a Security Feature
When onerous security protocols are replaced with invisible zero trust, usability and security improve. The strongest security teams aren’t the ones creating the most controls. They’re the ones enabling the mission to move faster, safely.
Ready to build invisible zero trust?





