By Dave Howard,
Senior Director, Cyber Operations
and James Dieteman
Director, Adversary Pursuit
Today’s cybersecurity environments are rich in data but poor in connection.
Security teams collect telemetry from vast sources: endpoints, networks, cloud platforms, identity systems, and third-party tools. Each produces signals. Few produce shared understanding.
The result? Limited clarity about which threats matter most and what actions will reduce risk, even as you field capable teams, strong tools, and seemingly endless activity.
This is where “Connected Intelligence” changes the equation, tipping the scales in defenders’ favor. When cyber threat intelligence (CTI) is connected across tools, teams, and decisions, it becomes more than an input, it becomes the backbone of effective cyber defense. Intelligence stops living at the edges of the organization and begins shaping how security work actually gets done. This is how connected intelligence drives security.

“When cyber threat intelligence (CTI) is connected across tools, teams, and decisions, it becomes more than an input, it becomes the backbone of effective cyber defense”
The Risk of Disconnected Intelligence
Most organizations already consume threat intelligence in some form. The challenge isn’t access to information, but what happens after that information arrives.
In disconnected environments, intelligence rarely reaches the point of impact. Teams work hard, but in isolation:
- Detection engineers develop alerts that are not based on real-world adversary activity
- Security operations center (SOC) analysts investigate alerts without knowing which adversaries are active or relevant
- Threat hunters cast wide nets instead of pursuing specific activities
- Security engineers harden systems based on generalized best practices
- Leaders struggle to align resources to real-world threats
Adversaries operate differently. They act with a shared understanding of targets, tools, and objectives. When CTI is connected across the security organization, it restores that shared understanding for defenders, allowing teams to move with greater clarity and coordination.
What Connected Intelligence Means for CTI
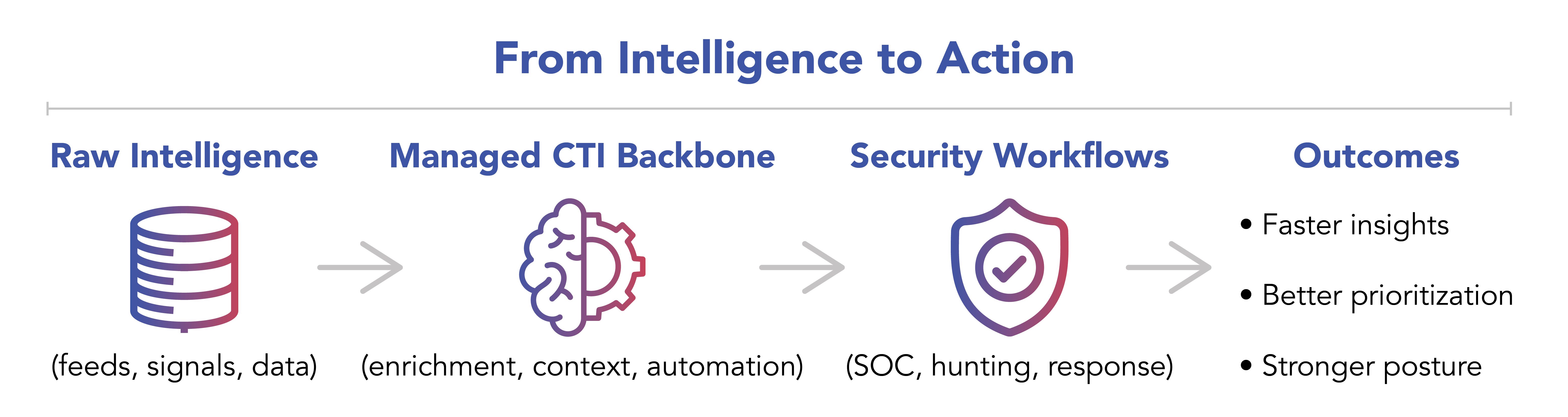
Connected Intelligence is about continuously linking intelligence to action across security operations.
In practice, this means CTI informs daily work, not just periodic reviews. Adversary context is available inside SOC workflows. Threat hunts are shaped by active campaigns and techniques. Engineering decisions enhance security based on how attackers actually operate. Response actions align to mission impact and risk.
“Instead of intelligence being reviewed in reports or dashboards, it flows through the entire security operation. CTI becomes connective tissue, ensuring every team works from the same intelligence picture”
Why CTI Often Struggles to Connect
When CTI fails to deliver on its promise, the problem is typically operational in nature. In fact, organizations often face the same friction points:
Without connection, intelligence becomes another source of noise. This results in missed threats, inefficient resource allocation, and fragmented response. When intelligence is embedded, automated, and shared, it becomes a force multiplier.
How ECS Delivers Connected Intelligence in Practice
ECS approaches CTI as an operational system designed to connect people, platforms, and decisions. Our Connected Intelligence approach ensures CTI is:
Enriched with mission-specific and environmental context
Integrated directly into SOC, hunting, and engineering workflows
Embedded into strategic decision-making processes
Delivered at operational speed through automation and orchestration
Continuously evolving as threats, technologies, and missions change
Rather than adding more tools, ECS connects existing investments through intelligence, so every security action is informed by what adversaries are doing.
This approach ensures intelligence translates into meaningful security outcomes.
CTI as a Managed Intelligence Backbone
Building and sustaining a connected CTI capability requires more than access to intelligence feeds or periodic analysis. It demands continuous integration, enrichment, automation, and expertise. For many organizations operating in complex or regulated environments, maintaining that level of capability internally can quickly strain both budgets and teams.
ECS delivers CTI as a managed intelligence backbone that supports the entire security ecosystem. Instead of asking organizations to build and maintain their own intelligence infrastructure, ECS provides a fully operationalized capability that connects intelligence directly to day-to-day security workflows. Intelligence is continuously enriched with mission-specific and environmental context, ensuring it remains relevant to the organization’s unique risk profile.
Because CTI is embedded across SOC operations, threat hunting, engineering, and response functions:
- Insights move quickly to the people and systems that need them
- Automation and orchestration help intelligence keep pace with adversaries
- Experienced intelligence professionals oversee analysis, validation, and refinement
By managing CTI as a shared operational foundation, ECS enables security teams to focus on defending critical assets rather than managing feeds and platforms. The result is clearer prioritization, stronger alignment across teams, and a more resilient security posture, driven by connected intelligence that translates insight into action.
When Intelligence Is Connected, Security Becomes Resilient
Cybersecurity doesn’t break down because teams lack tools or effort. It breaks down when intelligence is fragmented and not integrated into daily operations.
When CTI connects data, teams, and decisions, security becomes focused, adaptive, and resilient. Detections are more meaningful. Hunts are more precise. Responses are better aligned to risk. And every action is grounded in shared understanding.